A large-scale Android ad fraud operation dubbed “SlopAds” has been disrupted after 224 malicious apps on Google Play were used to generate 2.3 billion ad requests per day.
HUMAN's Satori Threat Intelligence team discovered the ad fraud campaign. The team reports that the apps have been downloaded more than 38 million times and use obfuscation and stealth techniques to hide their malicious behavior from Google and security tools.

Nearly 224 malicious apps linked to SlopAds ad fraud campaign.
The campaign was deployed globally , with app installs from 228 countries and SlopAds traffic accounting for 2.3 billion bid requests per day. The highest concentration of ad impressions came from the United States (30%), followed by India (10%) and Brazil (7%).
“Researchers dubbed this operation ‘SlopAds’ because the apps associated with this threat have a mass-produced appearance, resembling an ‘AI slop,’ and refer to the collection of AI-themed apps and services hosted on the threat actor’s C2 server,” HUMAN explained.
Extremely sophisticated advertising fraud
Ad fraud involves multiple levels of evasion tactics to avoid detection by Google's app review process and security software.
If a user installs the SlopAd app organically through the Play Store, and not from one of the campaign's ads, the app will behave like a normal app, performing the advertised function as normal.
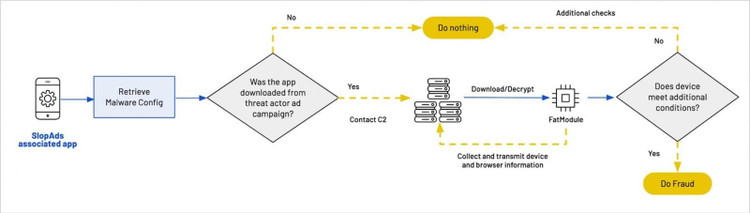
However, if it determines the app was installed by a user clicking on a link to it through one of the threat actor's ad campaigns, the software will use Firebase Remote Config to download an encrypted configuration file containing the URL for the ad fraud malware module, the cash-out server, and the JavaScript payload.
The app then determines whether it was installed on a legitimate user's device, rather than being analyzed by a researcher or security software.
If the app passes these checks, it downloads four PNG images that use steganography to hide parts of the malicious APK, which are used to carry out the ad fraud campaign itself.
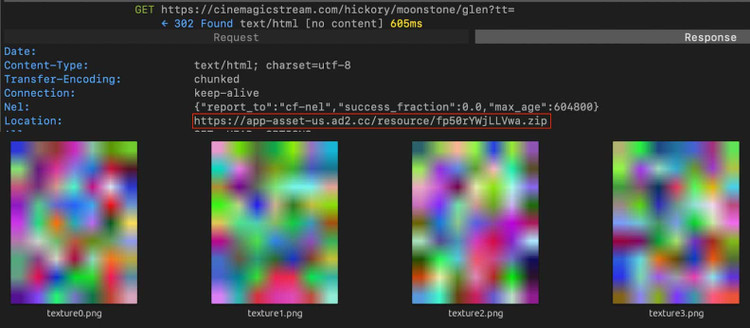
Once downloaded, the image is decrypted and re-installed on the device to form the complete "FatModule" malware, which is used to perform ad fraud.
Once FatModule is activated, it uses a hidden WebView to collect device and browser information, then navigates to ad fraud (money-scraping) domains controlled by the attacker.
This causes the device to continuously consume resources including data traffic as well as battery life and memory for accessing silent advertising sites.
These domains impersonate games and new websites, continuously displaying ads through hidden WebView screens to generate over 2 billion fraudulent ad impressions and clicks per day, thereby generating revenue for the attackers.
HUMAN said the campaign's infrastructure included multiple command-and-control servers and more than 300 associated advertising domains, suggesting the attackers were planning to expand their reach beyond the initial 224 apps identified.
Google has since removed all SlopAds apps from the Play Store, and Android's Google Play Protect has been updated to warn users to uninstall any apps present on their devices.
However, HUMAN warns that the sophistication of the ad fraud campaign suggests the attacker will likely adapt its plan to try again in future attacks.
If you accidentally download an app, you don't need to worry about tracking it down yourself. However, users need to pay attention on their devices, the system will appear a notification and ask to remove it.
This is because Google has updated its built-in Android security app Google Play Protect to warn users to uninstall any malicious apps that may be on their smartphones or tablets.
Source: https://khoahocdoisong.vn/kiem-tra-ngay-224-ung-dung-doc-hai-vua-bi-google-go-bo-post2149053682.html






![[Photo] Science and Technology Trade Union honors exemplary workers and excellent union officials](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/9/17/842ff35bce69449290ec23b75727934e)
![[Photo] General Secretary To Lam chairs a working session with the Standing Committee of the Government Party Committee](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/9/17/cf3d855fdc974fa9a45e80d380b0eb7c)
























































































Comment (0)